To fear love is to fear life, and those who fear life are already three parts dead.
Wednesday 30 November 2011
heap OLED display for your TI Launchpad
The guys over at the 43oh forums have been working on an OLED display booster pack for the TI Launchpad. The booster pack is now available in the 43oh store and is pretty cheap to boot.
The TI Launchpad is an awesome little dev board with a ravenous fan base. We’ve seen a lot of projects on Hack a Day use a Launchpad – everything from intervalometers to chicken coops. Unfortunately, the MSP430 doesn’t have the market penetration of the ‘board that shall remained unnamed,’ so it’s not very common to see a new Launchpad “shield.”
[bluehash] on the 43oh forums has been hard at work for the past month to put together his OLED booster pack. The display is 128×64 pixels with an incredible amount of brightness that we would expect from an OLED display. The software for the display is based on the SSD1306 driver with two font packs – Courier New large and small. Not a bad little piece of kit for an under appreciated dev board.
alculating Pi to 10 Trillion Digits; the last number is 5
In August, 2010, [Alexander Yee] and [Shigeru Kondo] won a respectable amount of praise for calculating pi to more digits than anyone else. They’re back again, this time doubling the number of digits to 10 Trillion.
The previous calculation of 5 Trillion digits of Pi took 90 days to calculate on a beast of a workstation. The calculations were performed on 2x Xeon processors running at 3.33 GHz, 96 Gigabytes of RAM, and 32 Terabytes worth of hard drives. The 10 Trillion digit attempt used the same hardware, but needed 48 Terabytes of disk to store everything.
Unfortunately, the time needed to calculate 10 Trillion digits didn’t scale linearly. [Alex] and [Shigeru] waited three hundred and seventy-one days for the computer to finish the calculations. The guys used y-cruncher, a multithreaded pi benchmarking tool written by [Alex]. y-cruncher calculates hexadecimal digits of pi; conveniently, it’s fairly easy to find the nth hex digit of pi for verification.
If you’re wondering if it would be faster to calculate pi on a top 500 supercomputer, you’d be right. Those boxes are a little busy predicting climate change, nuclear weapons yields, and curing cancer, though. Doing something nobody else has ever done is still an admirable goal, especially if it means building an awesome computer.
ANT+ networks using an MSP430 chip and Android phone
Jbremnant] wanted to try his hand with ANT+ wireless networks. This protocol is designed for light-weight and low-power consumer electronics, like heart rate chest straps and bicycle computers (Garmin brand devices for example). There are already libraries out there for Arduino, but [Jbremnant] found that most of them were written as slave-only code. He set out to use an MSP430 to drive a fully functioning ANT network including a computer and an Android phone.
The TI Launchpad is used as the master node in the network. [Jbremnant] chose the smaller of the two MSP430 processors that came with the dev platform. After starting down this road he realized that chip didn’t have a hardware UART needed to communicate with the SparkFun ANT board (based on the nRF24AP1 radio chip). Rolling with the punches, he used a software UART he had previously worked with. Now he’s able to transmit test data from the Launchpad. It is picked up by both a USB dongle on his computer and the Android phone seen above. Check out his demo video after the break.
http://www.youtube.com/watch?feature=player_embedded&v=ck9I86ENKLI
Mark your Territory
Although Dogs and other animals love to mark their territory with urine, this technique has been generally ignored by human beings. Despair no more, fellow homo sapiens, we have now developed the ability to check-in on foursquare through your information stream. This device is descriptively called “Mark your Territory.”
Although this is not currently available to buy in stores (although apparently $10,000 will get you one built), [Instructables] user [blorgggggg] has furnished directions on building your own. The system is powered by an Arduino and an Android phone. The urine tags have both a pointed end for sticking in grass and the like, and a sticky back to be used in a “more urban settings.”
The video after the break gives quite a bit of background trying to justify such a system in terms of communicating in the physical world, animals, et cetera, but it’s doubtful that this excuse will get you out of a public urination charge. You’ve been warned.
http://www.youtube.com/watch?feature=player_embedded&v=rRdfeb7vDWg
Although this is not currently available to buy in stores (although apparently $10,000 will get you one built), [Instructables] user [blorgggggg] has furnished directions on building your own. The system is powered by an Arduino and an Android phone. The urine tags have both a pointed end for sticking in grass and the like, and a sticky back to be used in a “more urban settings.”
The video after the break gives quite a bit of background trying to justify such a system in terms of communicating in the physical world, animals, et cetera, but it’s doubtful that this excuse will get you out of a public urination charge. You’ve been warned.
http://www.youtube.com/watch?feature=player_embedded&v=rRdfeb7vDWg
G35 LED Christmas Light Review and Teardown
[Todd Harrison] took a slew of pictures in his quest to loose all the secrets of the G-35 Christmas Lights. These are a string of 50 plastic bulbs which house individually addressable RGB LEDs. We’ve seen a ton of projects that use them, starting about a year ago with the original reverse engineering and most recently used to make a 7×7 LED matrix. But most of the time the original control board is immediately ditched for a replacement. It’s become so common that you can now buy a drop-in board, no hacking needed. We enjoy the hard look that [Todd] took at the electronics.
The stock controller uses a single layer, single sided board. There’s a resin-blob chip, but also an SOP-20 microcontroller. Since [Todd's] using several strings of lights on his house, he wondered if it would be possible to improve on the controller in order to synchronize the strands. His investigation showed that the board was designed to host a crystal oscillator but it is unpopulated. Unfortunately you can’t just add those parts to improve the timing of the chip (firmware changes would also be requires). He found that there’s a spot for a push-button. Quickly shorting the pads cycles through the effects, shorting them for a longer time turns off the string of lights. There is wireless control, but it seems that the only functionality it provides is the same as the unpopulated switch.
We enjoyed the close-up circuit board photos, and we like the spacing jig he used to attach the lights to his fascia boards. We’ve embedded a lengthy video about his exploits after the break.
The stock controller uses a single layer, single sided board. There’s a resin-blob chip, but also an SOP-20 microcontroller. Since [Todd's] using several strings of lights on his house, he wondered if it would be possible to improve on the controller in order to synchronize the strands. His investigation showed that the board was designed to host a crystal oscillator but it is unpopulated. Unfortunately you can’t just add those parts to improve the timing of the chip (firmware changes would also be requires). He found that there’s a spot for a push-button. Quickly shorting the pads cycles through the effects, shorting them for a longer time turns off the string of lights. There is wireless control, but it seems that the only functionality it provides is the same as the unpopulated switch.
We enjoyed the close-up circuit board photos, and we like the spacing jig he used to attach the lights to his fascia boards. We’ve embedded a lengthy video about his exploits after the break.
Tuesday 29 November 2011
Computer Hacking
Introduction
Unlike most computer crime / misuse areas which are clear cut in terms of actions and legalities (e.g. softwarepiracy), computer hacking is more difficult to define. Computer hacking always involves some degree of infringement on the privacy of others or damage to computer-based property such as files, web pages or software. The impact of computer hacking varies from simply being simply invasive and annoying to illegal. There is an aura of mystery that surrounds hacking,and a prestige that accompanies being part of a relatively "elite" group of individuals who possess technological savvy and are willing to take the risks required to become a true "hacker". An interesting alternative view of how hackers positively impact areas such as software development and hacker ideology is presented in Technology and Pleasure: Considering Hacking Constructive.
Even attempting to define the term "hacker" is difficult. Perhaps the premiere WWW resource in introducing individuals to hacking is the The New Hacker's Dictionary (http://www.logophilia.com/jargon/jargon_toc.html), a resource which encompasses everything from hacker slang, jargon, hacker folklore, writing style and speech to general appearance, dress, education and personality characteristics. According to TheNew Hacker's Dictionary, a hacker can be defined as:
A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary.
One who programs enthusiastically (even obsessively) or who enjoys programming rather than just theorizing about programming.
A person capable of appreciating hack value.
A person who is good at programming quickly.
An expert at a particular program, or one who frequently does work using it or on it.
An expert or enthusiast of any kind. One might be an astronomy hacker, for example.
One who enjoys the intellectual challenge of creatively overcoming or circumventing limitations.
[deprecated] A malicious meddler who tries to discover sensitive information by poking around. Hence 'password hacker', 'network hacker'. The correct term for this sense is cracker.
Even within hacker society, the definitions range from societally very positive (dare I say characteristic of gifted and talented individuals) to criminal. In his book, "Fighting Computer Crime: A New Framework for Protecting Information" (1998), Donn B. Parker lists two basic principles hacker live by:
The belief that information sharing is a powerful good and that it is the ethical duty of hackers to share their expertise by writing free software and facilitating access to information and to computing resources whenever possible.
The belief that system cracking for fun and exploitation is ethically OK as long as the cracker commits no theft, vandalism or breach of confidentiality.
Parker differentiates between benign and malicious hackers based on whether damage is performed, though in reality all hacking involves intrusion and a disregard for the efforts, works and property of others.
Issues
A number of issues arise in considering hacking from the educator perspective. First, we need to consider the fact that the public perception of hackers is mixed, and that "hacking" and "being considered a hacker" can be quite appealing to students who are going through developmental periods in which they are defining themselves, as well as challenging authority and rules. There is often a Robin Hood mentality to early actions, though it is unclear exactly who "the poor" are, and how they are "beingcompensated". Second, the anonymity of actions which hackers perform against others often enhances the severity of actions. For example, an adolescent who would never consider picking someone's pocket or physically damaging someone else's property or home, might be quite willing to steal people's credit card numbers or destroy poorly protected business or government files, since files and credit card numbers are not tangible entities, and the damage is done anonymously.
The media often presents these individuals in a glamorous light. Adolescents may fantasize about their degree of technological skills and, lacking the social skills required to be accepted well by others, move online in search of those who profess to have technological skills the students desire. A simple search using the term "hacker" with any search engine results in hundreds of links to illegal serial numbers, ways to downloadand pirate commercial software, etc. Showing this information off to others may result in the students being considered a "hacker" by their less technologically savvy friends, further reinforcing antisocial behavior. In some cases, individuals move on to programming and destruction of other individuals programs through the writing of computer viruses and Trojan horses, programs which include computer instructions to execute a hacker's attack. If individuals can successfully enter computers via a network, they may be able to impersonate an individual with high level security clearance access to files, modifying or deleting them or introducing computer viruses or Trojan horses. As hackers become more sophisticated,they may begin using sniffers to steal large amounts of confidential information, become involved in burglary of technical manuals, larceny or espionage.
Ways to Minimize Potential for Hacking
There are a number of ways for schools to minimize potential for hacking.
Schools need to clearly establish acceptable use policies and delineate appropriate and inappropriate actions to both students and staff.
Students and staff need to instructed regarding hacking, the mentality associated with it, the consequences of various hacking actions and possible consequences of interacting and forming online relationships with anonymous individuals who claim to be proficient in invading others' privacy.
The use of filters may be considered in reducing access to unauthorized software serial numbers and hacking-related materials, newsgroups, chatrooms and hacking organizations.
Teachers need to be aware of student activities in the computer labs and pay special attention to things they hear in terms of hacking behavior.
Many schools have taken intiative in having teachers work with technology-oriented students who exhibit many of the characteristics which may eventually lead to hacking-type behaviors. Recent web-based activities and competitions, including ThinkQuest, Web to the Edge and ExploraVision, are outstanding opportunities for these and other technologically oriented students to utilize their interests, energies and abilities in a postive way.
Unlike most computer crime / misuse areas which are clear cut in terms of actions and legalities (e.g. softwarepiracy), computer hacking is more difficult to define. Computer hacking always involves some degree of infringement on the privacy of others or damage to computer-based property such as files, web pages or software. The impact of computer hacking varies from simply being simply invasive and annoying to illegal. There is an aura of mystery that surrounds hacking,and a prestige that accompanies being part of a relatively "elite" group of individuals who possess technological savvy and are willing to take the risks required to become a true "hacker". An interesting alternative view of how hackers positively impact areas such as software development and hacker ideology is presented in Technology and Pleasure: Considering Hacking Constructive.
Even attempting to define the term "hacker" is difficult. Perhaps the premiere WWW resource in introducing individuals to hacking is the The New Hacker's Dictionary (http://www.logophilia.com/jargon/jargon_toc.html), a resource which encompasses everything from hacker slang, jargon, hacker folklore, writing style and speech to general appearance, dress, education and personality characteristics. According to TheNew Hacker's Dictionary, a hacker can be defined as:
A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary.
One who programs enthusiastically (even obsessively) or who enjoys programming rather than just theorizing about programming.
A person capable of appreciating hack value.
A person who is good at programming quickly.
An expert at a particular program, or one who frequently does work using it or on it.
An expert or enthusiast of any kind. One might be an astronomy hacker, for example.
One who enjoys the intellectual challenge of creatively overcoming or circumventing limitations.
[deprecated] A malicious meddler who tries to discover sensitive information by poking around. Hence 'password hacker', 'network hacker'. The correct term for this sense is cracker.
Even within hacker society, the definitions range from societally very positive (dare I say characteristic of gifted and talented individuals) to criminal. In his book, "Fighting Computer Crime: A New Framework for Protecting Information" (1998), Donn B. Parker lists two basic principles hacker live by:
The belief that information sharing is a powerful good and that it is the ethical duty of hackers to share their expertise by writing free software and facilitating access to information and to computing resources whenever possible.
The belief that system cracking for fun and exploitation is ethically OK as long as the cracker commits no theft, vandalism or breach of confidentiality.
Parker differentiates between benign and malicious hackers based on whether damage is performed, though in reality all hacking involves intrusion and a disregard for the efforts, works and property of others.
Issues
A number of issues arise in considering hacking from the educator perspective. First, we need to consider the fact that the public perception of hackers is mixed, and that "hacking" and "being considered a hacker" can be quite appealing to students who are going through developmental periods in which they are defining themselves, as well as challenging authority and rules. There is often a Robin Hood mentality to early actions, though it is unclear exactly who "the poor" are, and how they are "beingcompensated". Second, the anonymity of actions which hackers perform against others often enhances the severity of actions. For example, an adolescent who would never consider picking someone's pocket or physically damaging someone else's property or home, might be quite willing to steal people's credit card numbers or destroy poorly protected business or government files, since files and credit card numbers are not tangible entities, and the damage is done anonymously.
The media often presents these individuals in a glamorous light. Adolescents may fantasize about their degree of technological skills and, lacking the social skills required to be accepted well by others, move online in search of those who profess to have technological skills the students desire. A simple search using the term "hacker" with any search engine results in hundreds of links to illegal serial numbers, ways to downloadand pirate commercial software, etc. Showing this information off to others may result in the students being considered a "hacker" by their less technologically savvy friends, further reinforcing antisocial behavior. In some cases, individuals move on to programming and destruction of other individuals programs through the writing of computer viruses and Trojan horses, programs which include computer instructions to execute a hacker's attack. If individuals can successfully enter computers via a network, they may be able to impersonate an individual with high level security clearance access to files, modifying or deleting them or introducing computer viruses or Trojan horses. As hackers become more sophisticated,they may begin using sniffers to steal large amounts of confidential information, become involved in burglary of technical manuals, larceny or espionage.
Ways to Minimize Potential for Hacking
There are a number of ways for schools to minimize potential for hacking.
Schools need to clearly establish acceptable use policies and delineate appropriate and inappropriate actions to both students and staff.
Students and staff need to instructed regarding hacking, the mentality associated with it, the consequences of various hacking actions and possible consequences of interacting and forming online relationships with anonymous individuals who claim to be proficient in invading others' privacy.
The use of filters may be considered in reducing access to unauthorized software serial numbers and hacking-related materials, newsgroups, chatrooms and hacking organizations.
Teachers need to be aware of student activities in the computer labs and pay special attention to things they hear in terms of hacking behavior.
Many schools have taken intiative in having teachers work with technology-oriented students who exhibit many of the characteristics which may eventually lead to hacking-type behaviors. Recent web-based activities and competitions, including ThinkQuest, Web to the Edge and ExploraVision, are outstanding opportunities for these and other technologically oriented students to utilize their interests, energies and abilities in a postive way.
Saturday 26 November 2011
Star Sword
The stunning sequel to the classic arcade shooter game pits you against the aliens in a ferocious battle to the death. Pilot your ship through five enormous galaxies and 50 futuristic 3D levels to find all the pieces of the secret weapon.
Download from the above link ...
http://www.gametop.com/download-free-games/star-sword/download.html
Download from the above link ...
http://www.gametop.com/download-free-games/star-sword/download.html
Download Free Full Version PC Game Police Supercars Racing
Sun City is the city of the future, but the rising crime rate makes this place dangerous for living. Extremists block roads, criminals crash cars and hackers override the city’s automatic traffic control. The Special Supercar Police Unit was organized to blow the whistle on these practices.
http://www.gametop.com/download-free-games/police-supercars-racing/download.html
http://www.gametop.com/download-free-games/police-supercars-racing/download.html
The best Anti Virus software 4 ur PC!!


Avira Free Antivirus
Our entry-level antivirus eliminates many forms of malware, including worms, rootkits and costly dialers.
DownloadFriday 25 November 2011
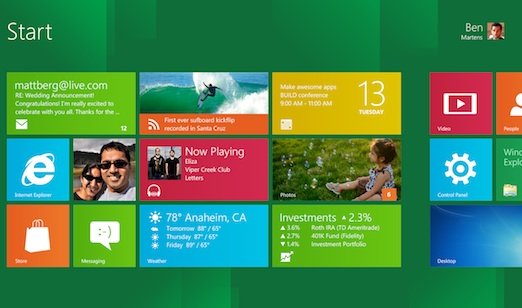
Windows 8 Beta
Windows 8 Beta is the pre-release version of the upcoming Microsoft Windows 8. Even before the launch of Windows 7, Microsoft started working for the next Windows version. Windows 7 has been considered as the Microsoft’s best Windows version so far. Moreover, Windows 7 captures the biggest market share in comparison to other Microsoft Windows version.
Microsoft, which people also say is the Software Giant as what they had bestowed to the tech world no other competing software maker has given. Thus, after seeing the success of Windows 7 at the peak Microsoft took a challenge itself to develop a Windows version which goes beyond imagination.
The challenge came in form of reimagining Windows which took the face of Windows 8 and before it gets released for the end users, Windows 8 beta will be released for testing purpose to find bugs and to check the functions whether they are properly working or not.
Windows 8 Beta Expected Release Date
Microsoft will be launching Windows 8 Beta before it launches the Windows 8 Release Candidate (RC). Windows 8 Beta is expected to arrive early January in 2012. Windows 8 beta will be made available to the general public for testing purpose to find out whether the functions are working appropriately or not.
Note, Windows 8 Beta is not the actual version as it might embed certain faults or bugs and thus to find those bugs and faults only this version is released.
Windows 8 Beta Download
Once Windows 8 beta gets released, it will be made available for download to the general public. If you are looking forward for Windows 8 Beta Download, then you are firstly required to register. We will update you with the registration links once they will be made available.
Windows 8 Beta Hardware Requirements
It is very much expected that Windows 8 Beta would be carrying almost the same hardware requirements that Windows 7 requires. We are here discussing the minimum hardware requirements.
Thus, expected minimum hardware requirements would be:
- 2 GHz or faster 64 bit (x64) processor.
- 1 Gigabyte (GB) or 2 GB RAM.
- 32 GB of available free hard disk space.
- DirectX 11 graphics device with WDDM 1.0 or higher driver.
Windows 8 Beta SKU’s
Microsoft launched Windows 7 with multiple SKU’s like Windows 7 Starter, Windows 7 Home Basic, Windows 7 Professional, Windows 7 Enterprise, Windows 7 Ultimate, and Windows 7 Home Premium.
Though Microsoft has not yet announced officially what SKU’s edition will be made for Windows 8,Steven Sinofsky says, “In the coming months, many folks will be testing pre-release builds of Windows 8. As everyone knows, two things are always the case early on. First, the software is not done and things will change—features will be added and removed. Second, the different editions or SKUs are not developed or announced until late in the development process.”
Thus, we can expect that Microsoft, if multiple SKU’s will be released, they will be named as Windows 8 Ultimate, and Windows 8 Professional, seeing Windows 7 SKU’s editions.
Windows 8 is a concept which goes beyond imagination, kudos to the complete Windows 8 building team for taking up the challenge and bringing an evolution in the computing world. Windows 8 beta is going to give the early taste of Windows 8, and its concept which is intended for both Tablets and PC’s.
On my quest to find the most useful things for Facebook I came across these 10 Facebook tips, tricks and add-ons, that might come in handy for the daily Facebook user.
Facebook Colour Changer for Firefox users
A user-script for the Firefox Add-on Greasemonkey that allows you to Change your Facebook Color Scheme from the default blue to any you choose using a color selector.
Facebook Colour Changer Script Download page
Facebook Colour Changer Script Download page
FFixer for Firefox users
A user-script for users with or without Greasemonkey that enables several enhancements such as bigger profile pictures, make viewing of photo albums easier, adds links to download videos, showing people’s ages and signs, Google Calendar integration, bookmarks, keyboard shortcuts and more.
FFixer Script Download page
FFixer Script Download page
KeepTube for Firefox users
A user-script that allows you to download YouTube Videos(HD 1080p & 720p), DailyMotion, Facebook, Vimeo and many more.
KeepTube Download page
A user-script that allows you to download YouTube Videos(HD 1080p & 720p), DailyMotion, Facebook, Vimeo and many more.
KeepTube Download page
Share on Facebook IE Accelerator
Quickly share webpages, links or on Facebook using the Right-Click menu in IE Accelerator Addon.
Download Add-On from the IE Gallery
Quickly share webpages, links or on Facebook using the Right-Click menu in IE Accelerator Addon.
Download Add-On from the IE Gallery
Facebook Taskbar Pinning with IE
If you’re a fan of pinning your favorite sites to the taskbar, Facebook is supported as well.
When you right-click the pinned icon in the taskbar you have options for News, Messages, Events, Friends, Facebook Home and Start Facebook in InPrivate Browsing.
More information on pinning a site to Taskbar available from the Internet Explorer Gallery page
If you’re a fan of pinning your favorite sites to the taskbar, Facebook is supported as well.
When you right-click the pinned icon in the taskbar you have options for News, Messages, Events, Friends, Facebook Home and Start Facebook in InPrivate Browsing.
More information on pinning a site to Taskbar available from the Internet Explorer Gallery page
For Fun
Just bored and wanting to have a little fun? Or maybe you’re a Pirates of the Caribbean Fan – then scroll to the bottom of your Facebook page in the Footer of the page where it displays your language, click it and you will be displayed with the language selector. Look for English on the Left and click it. Want to be a Pirate select English (Pirate) or if you just want to have some fun select English (Up-Side Down).
Just bored and wanting to have a little fun? Or maybe you’re a Pirates of the Caribbean Fan – then scroll to the bottom of your Facebook page in the Footer of the page where it displays your language, click it and you will be displayed with the language selector. Look for English on the Left and click it. Want to be a Pirate select English (Pirate) or if you just want to have some fun select English (Up-Side Down).
Facebook Comments
Add Facebook Comment Box to your Website\Blog
Visit the Facebook Developers Page to customize how your Comment Box will appear and get the code to use.
Add Facebook Comment Box to your Website\Blog
Visit the Facebook Developers Page to customize how your Comment Box will appear and get the code to use.
Facebook Keyboard Shortcuts
*Chrome and Opera do not require hitting the Enter Key
*Hitting Alt +/or? will automatically set to the Search Box. if you hit Enter it will bring you to the Search Page.
*Alt + M does not work in IE.
*Hitting Alt +/or? will automatically set to the Search Box. if you hit Enter it will bring you to the Search Page.
*Alt + M does not work in IE.
Chat Emoticons
- Hotmail
Log into Hotmail and on the top right toolbar click Options. Select More options
Under the heading Customize your Contacts, select Importing Contacts
Click the Facebook Icon and then select the options you want available
Click Connect with Facebook.
Under the heading Customize your Contacts, select Importing Contacts
Click the Facebook Icon and then select the options you want available
Click Connect with Facebook.
I have not used this but I am told it will send requests to each of your friends on Facebook.
- Gmail
You can use your Hotmail or Email account or any other that can connect to Facebook and create a CSV file that you can use to import contacts to Gmail but there is a quick way to generate this file.
Friends to Gmail will allow you to connect to Facebook and will generate a page with all your contacts. Just copy the text to Notepad and save as nameyouwant.csv.
Log into Gmail and click Contacts, click More Actions in the toolbar and click Import. Select your CSV file you can now import your Facebook friends to Gmail.
Friends to Gmail will allow you to connect to Facebook and will generate a page with all your contacts. Just copy the text to Notepad and save as nameyouwant.csv.
Log into Gmail and click Contacts, click More Actions in the toolbar and click Import. Select your CSV file you can now import your Facebook friends to Gmail.
- Yahoo
Log into your Yahoo Mail and on the left where the Contacts heading is listed click Add
Click the Facebook Icon with the heading, Import email addresses from your Facebook friends to Yahoo! Contacts.
Click the Facebook Icon and next you will be presented with a verification page, click Okay.
If you are logged into Facebook it will automatically retrieve your Facebook friends and add them to your Yahoo contacts.
Click the Facebook Icon with the heading, Import email addresses from your Facebook friends to Yahoo! Contacts.
Click the Facebook Icon and next you will be presented with a verification page, click Okay.
If you are logged into Facebook it will automatically retrieve your Facebook friends and add them to your Yahoo contacts.
These are just a few of the thousands of Add-on’s and Tricks available across the web for Facebook. If you know of any more such, please do share in the Comments.
Security tips for Facebook is something you may also want to have a look at!
Subscribe to:
Posts (Atom)